What’s the difference between a blogger and newspaper columnist?
The answer, more often than not, is that a blogger actually takes the time to investigate a story before committing their thoughts to teh Interwebs, unlike newspaper columnists, many of whom seem to think that the fact that they get paid for airing their opinions gives them an unfettered right to run off at the keyboard without first performing even the most cursory exercise in checking their facts.
Yesterday, the Telegraph published a typically formulaic rant on the subject of the alleged persecution of Christians by Cristina Odone, under the headline ‘The attack on FreeFaith.com shows the intolerance of religion’s enemies’ which concludes with the following allegation:
Now, they can’t. Last Friday, a sophisticated hacker embedded a malicious code in my FTP access, and disabled FreeFaith.com. I’m not pointing any fingers, but a review of the Tweets my appearance on Question Time prompted, reveals that my faith earns me some vicious enemies. The programme did not raise any religious questions; nor was I introduced as a Christian or even as the ex-editor of the Catholic Herald; yet the tweets are all about my being a “theocrat” and a “Christian apologist”. As such, I must be condemned – and silenced. So much for tolerance. So much for an easy life.
So Odone’s personal website falls over and, of course, its must be those damnably intolerant militant atheists/secularists who’re to blame… right?
Wrong.
For starters, Odone’s ‘Free Faith’ website has not be disabled at all, it’s still up and running but – and this is why I’m providing a link to the site – it has been flagged as unsafe by Google Safe Browsing since last Thursday (23rd February), which means that if you try to visit the site using Google’s Chrome Browser or Firefox you’ll get a message in your browser that looks something like this…
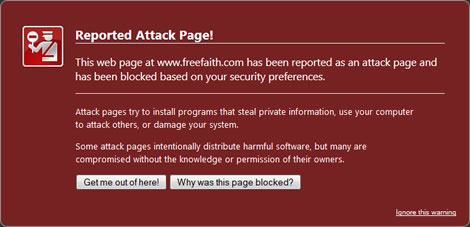
If you take the ‘Why was this page blocked?’ option you’ll discover that the reason that Google is blocking Odone’s site is because its been dropping malware onto its unsuspecting visitors. To be more specific, the site has been infected with/using the Blackhole Exploit Kit, a pretty sophisticated Russian ‘crimeware’ application which has been kicking around since the beginning of 2011.
How does this work?
Well, if you visit an infected site everything will appear to be prefectly normal. However, what you won’t have noticed is that in addition to given the content you’re expecting to get, the site will also have secretly opened a hidden IFrame to another website and its this hidden site that will busily download and install malicious software to your computer, using exploits in some older browser plugins. In the case of Odone’s website the hidden IFrames have been traced back to two different domains; acmetoy.com, which is hosted on a server in the Russian Federation, and h1x.com, which leads back to a Dynamic DNS service called change-ip.org
What kind of malicious software are we talking about here?
Well that depends entirely on the kind of payload the individual responsible for infecting Odone’s site wants to deliver. It could be a botnet client, a banking trojan, a keylogger, an adware server., whatever the individual using the kit wants to distribute.
Its a system that’s designed to facilitate criminal enterprises – amongst other things – and if you want to use an up to date version of the kit, it doesn’t come cheap – an annual license costs $1,500, a semi-annual licence costs $1,000 and you can pick up a quarterly licence for $700 and you can also rent the kit for anything from $50 for 24 hours up to $500 for four week, including a domain name and space on the author’s own server.
Older versions, with more limited capabilities, have also got into the wild and can be picked up free of charge via torrent networks and file hosting site, if you know what to look for.
Now, although I’ve described this as a sophisticated system, the sophistication is all in the design and development of the system – in use its all managed via a web browser and requires no great technical ability to pull off a scam. The system even has a built-in advertising module which allows users to advertise payload applications, such as banking trojans, for sale – and in case you’re not sure, a banking trojan is a piece of malware which tries to steal your bank account details and passwords.
Although Odone seems to believe that the sudden flagging of her site by Google Safe Browsing may be linked to her appearance on last week’s BBC Question Time, information obtained from an online malware scanning service suggests that this isn’t the case as the site has been flagged for delivering malware on at least three other occasions in the last 30 days – on February 7th, 11th and 18th.
This seems to indicate that the site was infected more than two weeks prior to her Question Time appearance and that it was flagged by Google on the same day only because that appearance, and the comments it generated on Twitter, acted to drive additional traffic to her site, increasing the chance that the infection would be detected.
Because the exploit system relies on visitors to an infected site having out of date plugins installed in the web browser, it will only be detected in operation when its either visited by someone who has those plugins and a virus scanner which is configured to report back any viruses/malware back to base or when its scanned by Google’s own automated system, which explains why Odone’s site can have been infected for at least 2-3 weeks before she, or anyone else, became aware of it.
In short. Odone’s website problems are nothing whatsoever to do with her appearance on Question Time or her religious beliefs, just good old fashioned criminality.
I await her retraction with some considerable interest.
Thanks for the comment you left.
My bet is she will ignore this and keep huffing that sweet crack-pipe of moral indignation
If you were largely untechnical and the same thing happened to you around the time you were getting some pretty nasty threats on twitter you might jump to the same conclusion. Why don’t you try to help her rather than just slate her?